






















Study with the several resources on Docsity

Earn points by helping other students or get them with a premium plan


Prepare for your exams
Study with the several resources on Docsity

Earn points to download
Earn points by helping other students or get them with a premium plan
Community
Ask the community for help and clear up your study doubts
Discover the best universities in your country according to Docsity users
Free resources
Download our free guides on studying techniques, anxiety management strategies, and thesis advice from Docsity tutors
computer networks pdf2 of class sessionpdf2 of class session
Typology: Slides
1 / 70

This page cannot be seen from the preview
Don't miss anything!































































Department of Computer Science & Software Engineering Concordia University, Montreal, Canada These slides has mainly been extracted, modified and updated from original slides of : Computer Networking: A Top Down Approach, 6th edition Jim Kurose, Keith Ross Addison-Wesley, 2013 Additional materials have been extracted, modified and updated from: Understanding Communications and Networking, 3e by William A. Shay 2005 Copyright © 1996- 2013 J.F Kurose and K.W. Ross Copyright © 2005 William A. Shay Copyright © 2018 Aiman Hanna All rights reserved
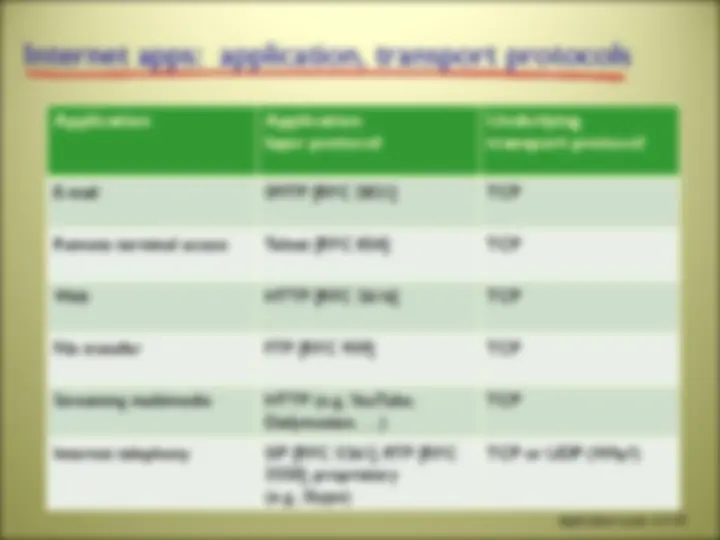
e-mail web text messaging remote login P2P file sharing multi-user network games streaming stored video (YouTube, Hulu, Netflix) E-commerce voice over IP (e.g., Skype) real-time video conferencing social networking search … …
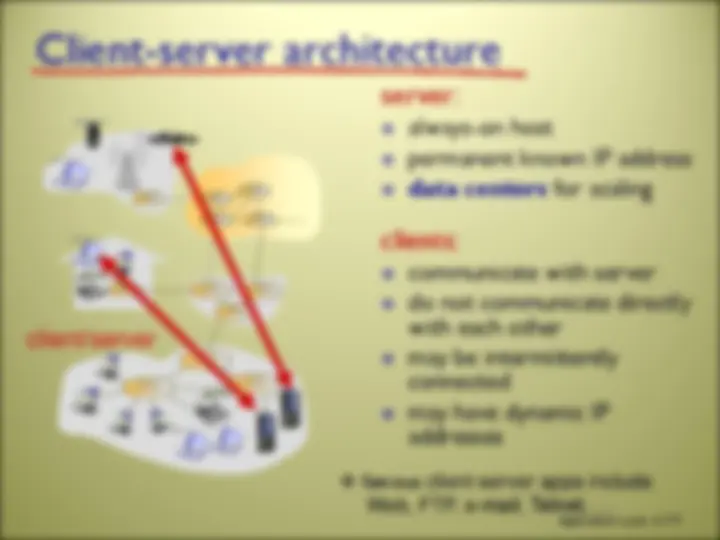
always-on host permanent known IP address data centers for scaling
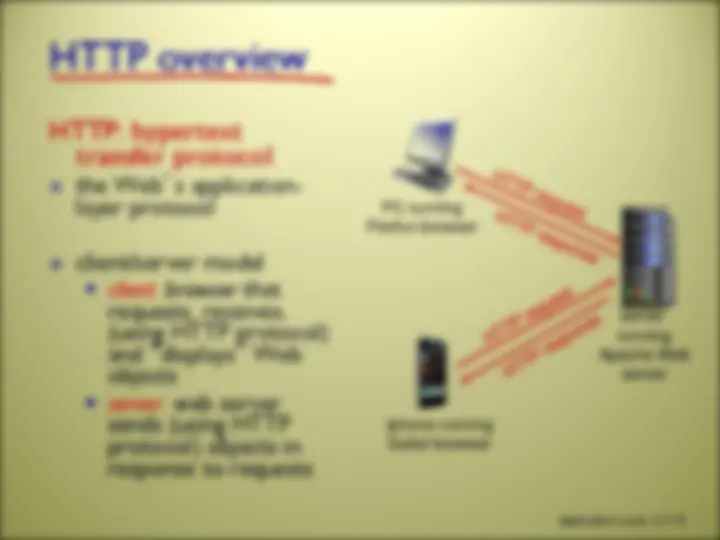
communicate with server do not communicate directly with each other may be intermittently connected may have dynamic IP addresses client/server famous client-server apps include Web, FTP, e-mail, Telnet, …
Cost-effective no need for server infrastructure and server bandwidth However, future P2P applications face 3 major challenges: ISP-Friendly : residential ISP (DSL, Cable, …) are asymmetric Security : a challenge, since P2P apps are highly distributed and naturally open Incentive : users must volunteer bandwidth, storage space and computational resources to P2P apps peer-peer
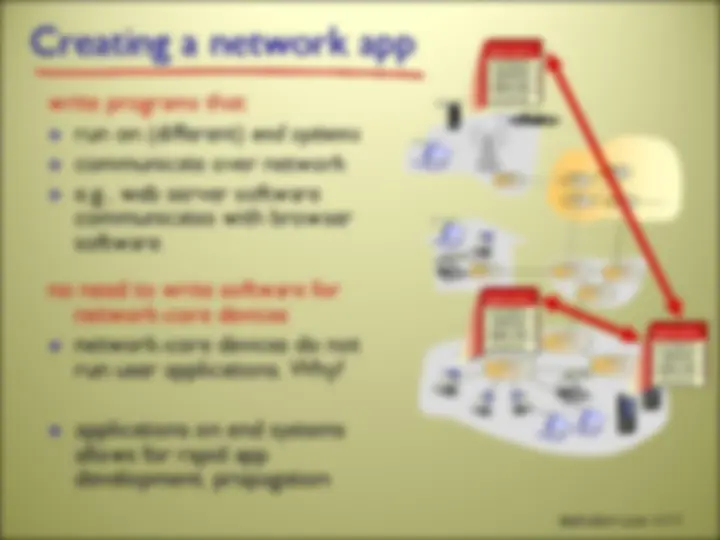
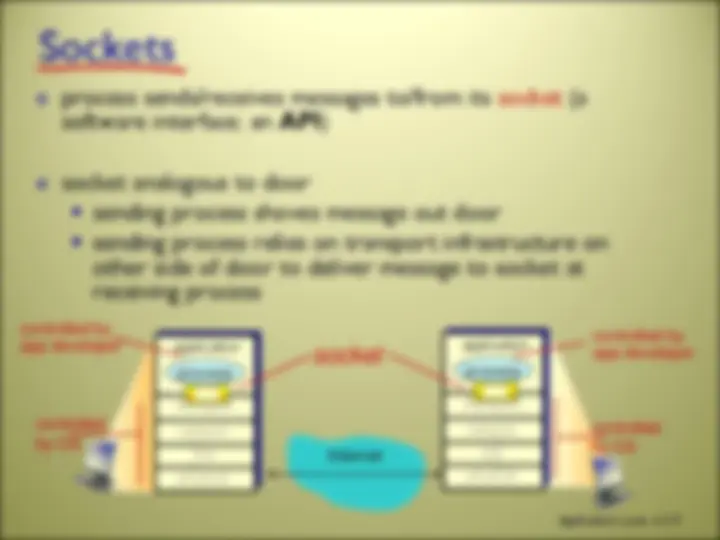
within same host, two processes communicate using inter-process communication (defined by OS) processes in different hosts communicate by exchanging messages
initiates communication
waits to be contacted aside: applications with P2P architectures have client processes & server processes
Addressing processes to receive messages, process must have identifier host device has unique 32- bit IP address Q: does IP address of host, on which process runs, suffice for identifying the receiving process (more precisely, the receiving socket)? identifier includes both IP address and port numbers associated with process on host. example port numbers: HTTP (web) server: 80 SMTP (mail) server: 25 to send HTTP message to gaia.cs.umass.edu web server: IP address: 128.119.245. port number: 80 more shortly… A: no, many network processes can be running on same host
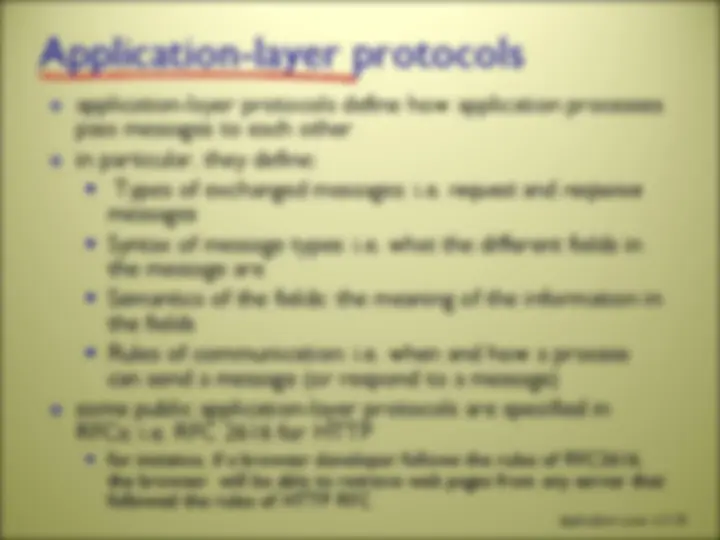
types of messages exchanged, e.g., request, response message syntax: what fields in messages & how fields are delineated message semantics meaning of information in fields rules for when and how processes send & respond to messages open protocols: defined in RFCs allows for interoperability e.g., HTTP, SMTP proprietary protocols: e.g., Skype
application data loss throughput time sensitive File transfer/download No loss Elastic No E-mail No loss Elastic No Web documents No loss Elastic (few kbps) No Real-time audio/video (i.e. Internet telephony, videoconferencing) Loss-tolerant Audio: 5kbps-1Mbps Video: 10 Kbps – 5 Mbps Yes; 100s ms Streaming stored audio/video Loss-tolerant Same as above; Yes; few seconds Interactive games Loss-tolerant few kbps – 10 Kbps Yes; 100s ms Text/Instant messaging No loss Elastic Yes and No
Internet transport protocols services
connection-oriented: setup required between client and server processes reliable transport between sending and receiving process flow control: sender won’t overwhelm receiver congestion control: throttle sender when network overloaded does not provide: timing, minimum throughput guarantee, security
unreliable data transfer between sending and receiving process does not provide: reliability, flow control, congestion control, timing, throughput guarantee, security, or connection setup Q: why bother? Why is there a UDP?
Securing TCP
no encryption cleartext passwords sent into socket traverse Internet in cleartext
provides encrypted TCP connection data integrity end-point authentication
Apps use SSL libraries, which “talk” to TCP
cleartext passwds sent into socket traverse Internet encrypted
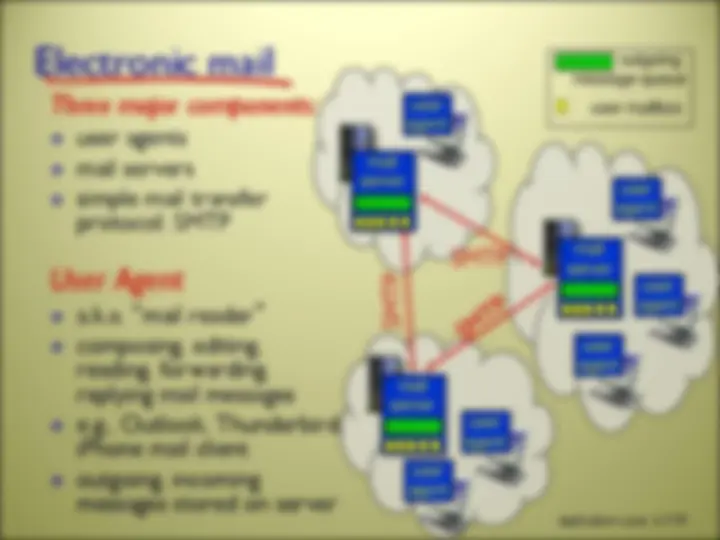
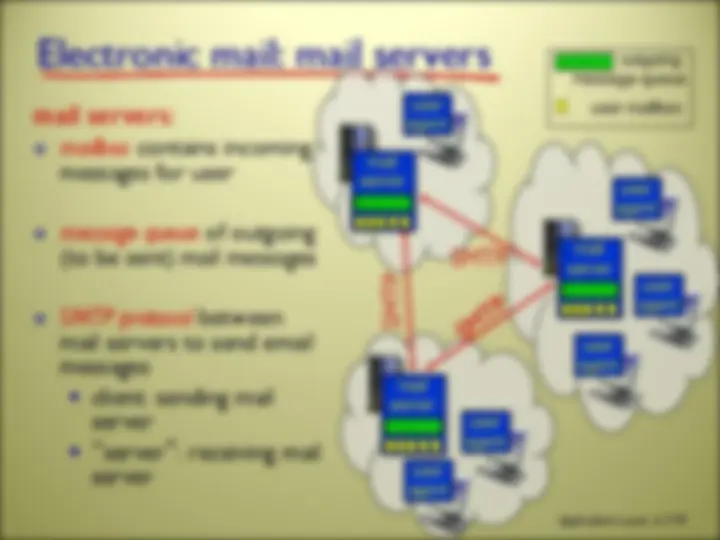
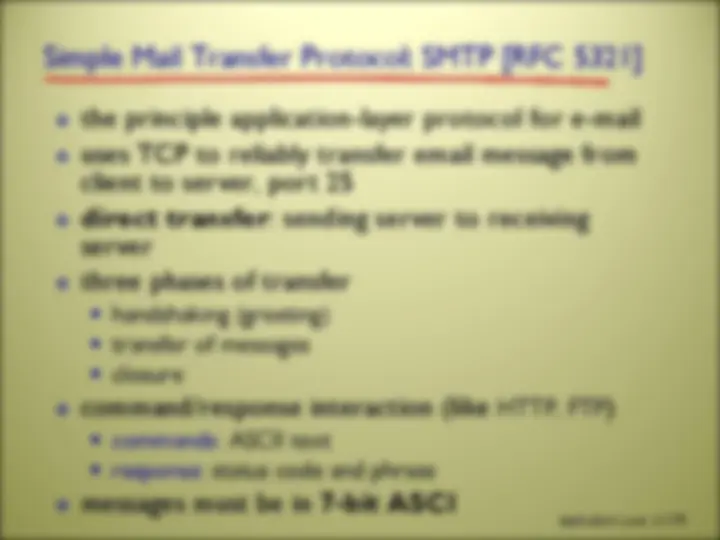
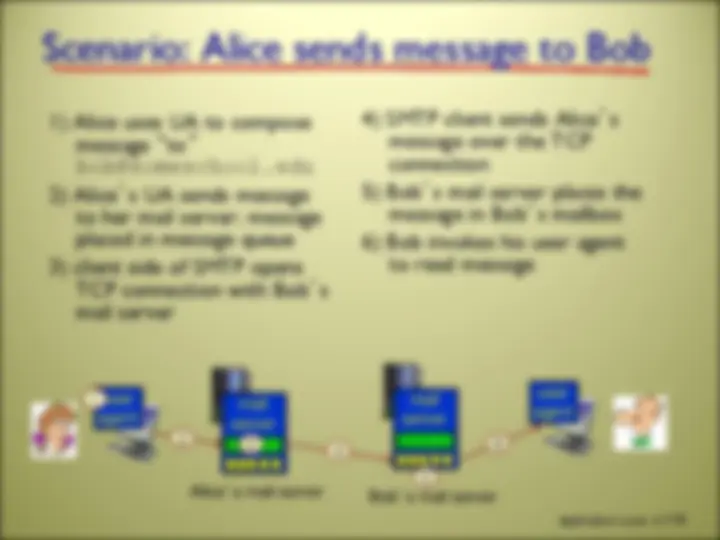
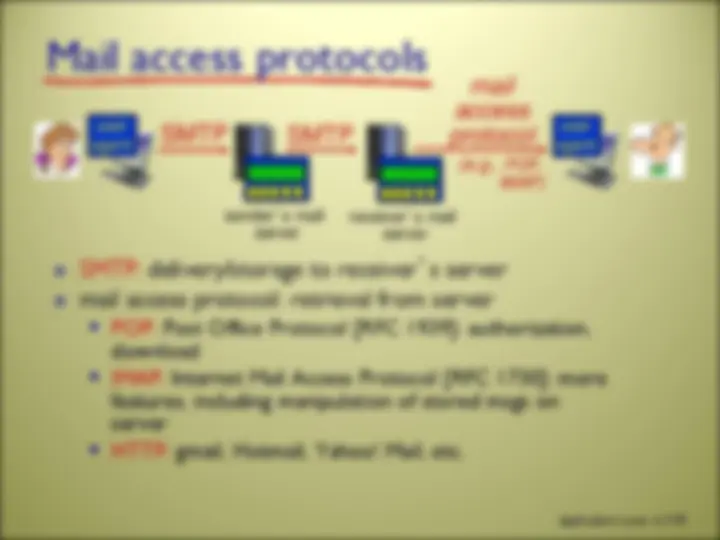
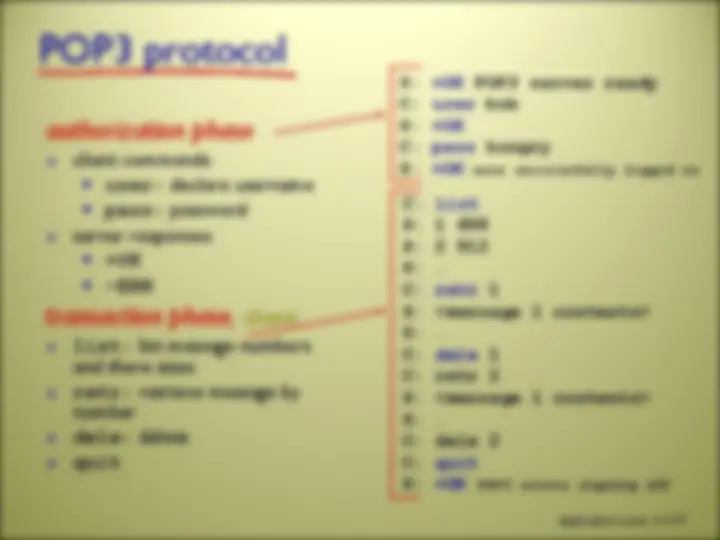
there are MANY network applications (possibly new ones are being written as you read these slides!) we will here look at 5 of the most important and pervasive network applications: Web and HTTP FTP Electronic Mail DNS P2P
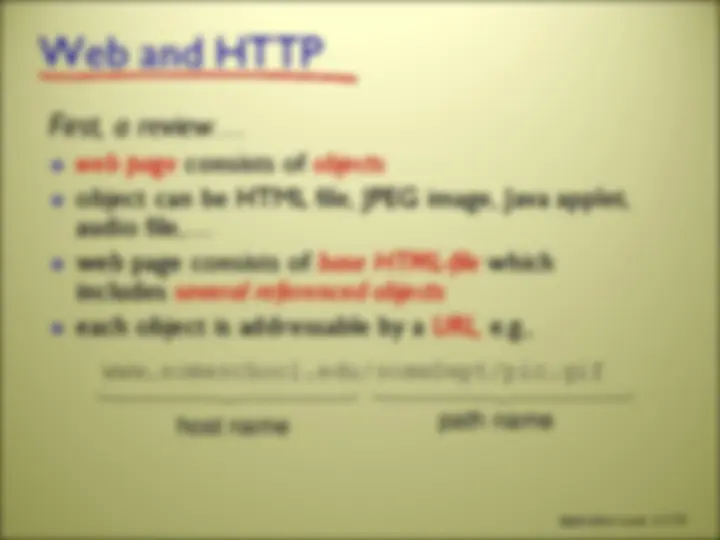
www.someschool.edu/someDept/pic.gif host name path name