Download Understanding User Accounts, Groups, and Permissions in Linux and more Summaries Computer Science in PDF only on Docsity!
Lession
User management and
Access Permission
Content
- User management
- Configuration files for user account and groups
- Root and sudo users
- User management utility
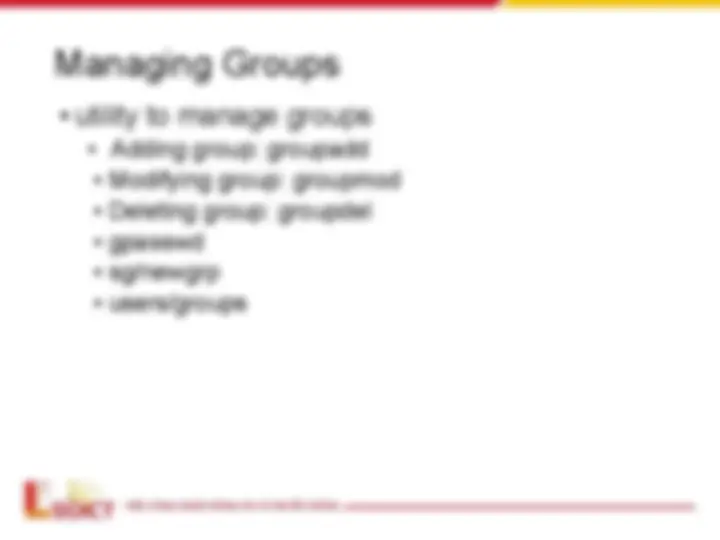
- Group management ultiliy
- Access Permission
- Introduction
- Directories and File Permission
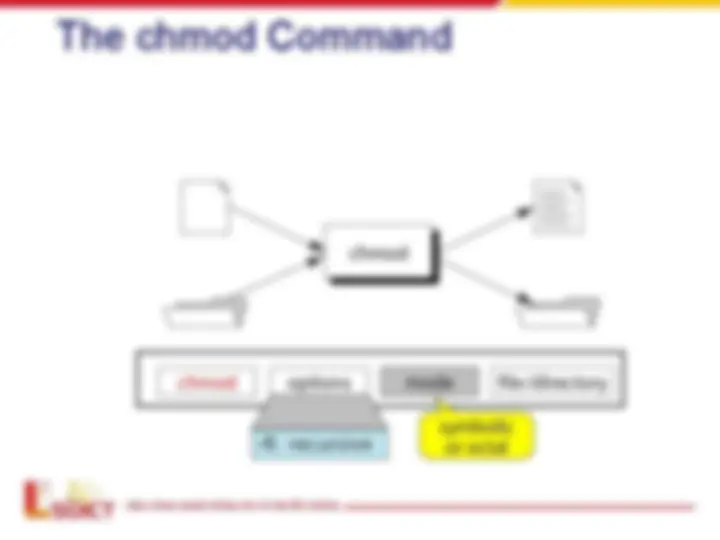
- Changing Permission
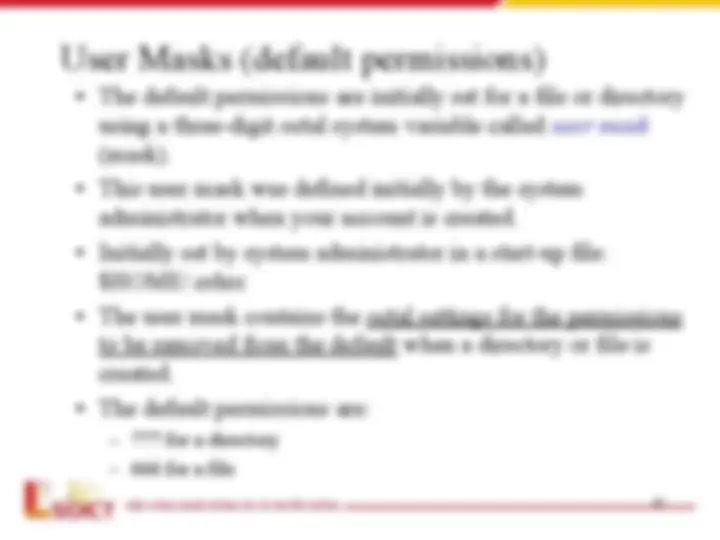
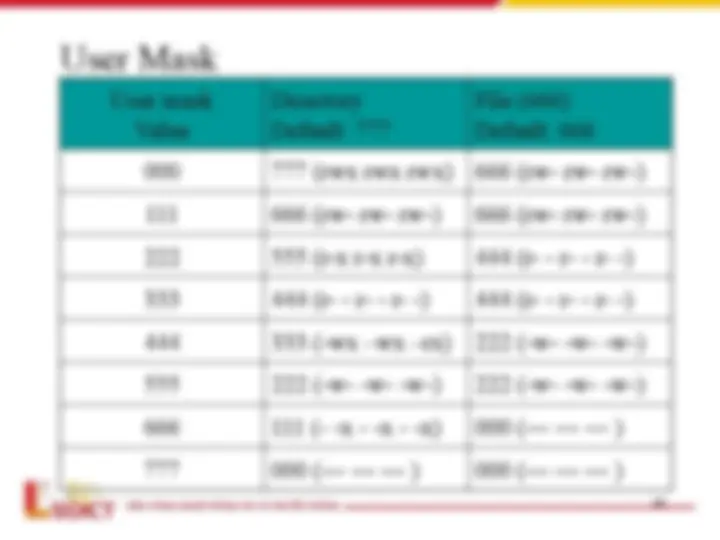
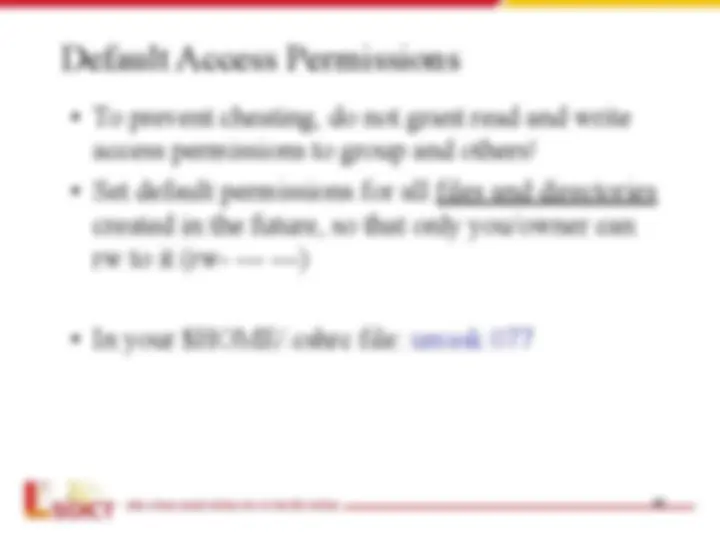
- User Masks
- Special Permissions
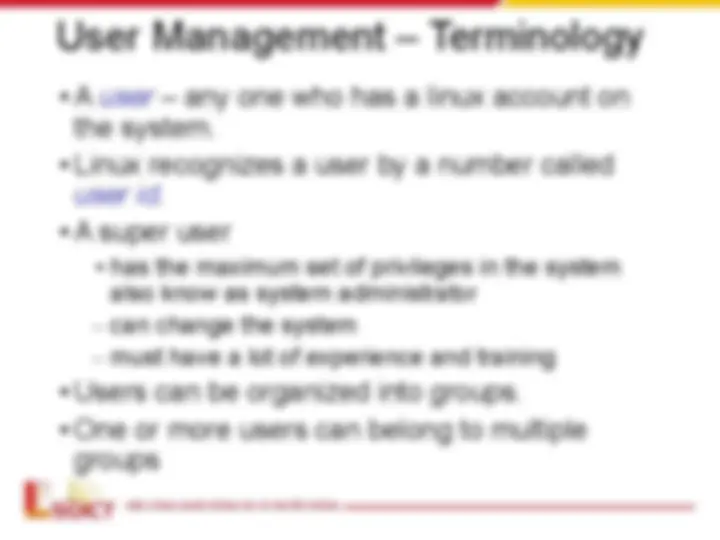
User Management – Terminology
- A user – any one who has a linux account on
the system.
- Linux recognizes a user by a number called
user id.
- A super user
- has the maximum set of privileges in the system
also know as system administrator
- can change the system
- must have a lot of experience and training
- Users can be organized into groups.
- One or more users can belong to multiple
groups
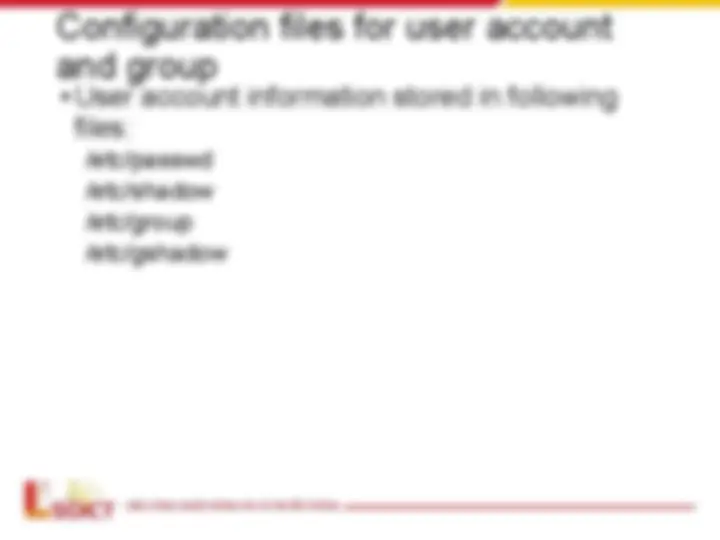
Configuration files for user account
and group
- User account information stored in following
files:
/etc/passwd
/etc/shadow
/etc/group
/etc/gshadow
/etc/passwd
Username:password:UID:GID:Info:Home:Shell
- Username: It is used when user logs in. It should be between 1 and 32 characters in length.
- Password: An x character indicates that encrypted password is stored in /etc/shadow file.
- User ID (UID): Each user must be assigned a user ID (UID). UID 0 (zero) is reserved for root and UIDs 1-99 are reserved for other predefined accounts. Further UID 100-999 are reserved by system for administrative and system accounts/groups.
- Group ID (GID): The primary group ID (stored in /etc/group file)
- User ID Info: The comment field. It allow you to add extra information about the users such as user's full name, phone number etc. This field use by finger command.
- Home directory: The absolute path to the directory the user will be in when they log in. If this directory does not exists then users directory becomes /
- Shell: The absolute path of a command or shell (/bin/bash). Typically, this is a shell. Please note that it does not have to be a shell. $ grep root /etc/passwd root:x:0:0:root:/root:/bin/bash operator:x:11:0:operator:/root:/sbin/nologin
/etc/shadow
Username:Password:Last_pwd_change:Minimum:Maximum:Warn:Inactive :Expire
- Username: It is your login name
- Password: It your encrypted password. The password should be minimum 6- characters long including special characters/digits
- Last password change: number of days since Jan 1, 1970 that password was last changed
- Minimum: The minimum number of days required between password changes i.e. the number of days left before the user is allowed to change his/her password
- Maximum: The maximum number of days the password is valid (after that user is forced to change his/her password)
- Warn : The number of days before password is to expire that user is warned that his/her password must be changed
- Inactive : The number of days after password expires that account is disabled
- Expire : days since Jan 1, 1970 that account is disabled i.e. an absolute date specifying when the login may no longer be used
$ grep root /etc/shadow root:b93.GT2r.7IZ6:9718:0:60:7:::
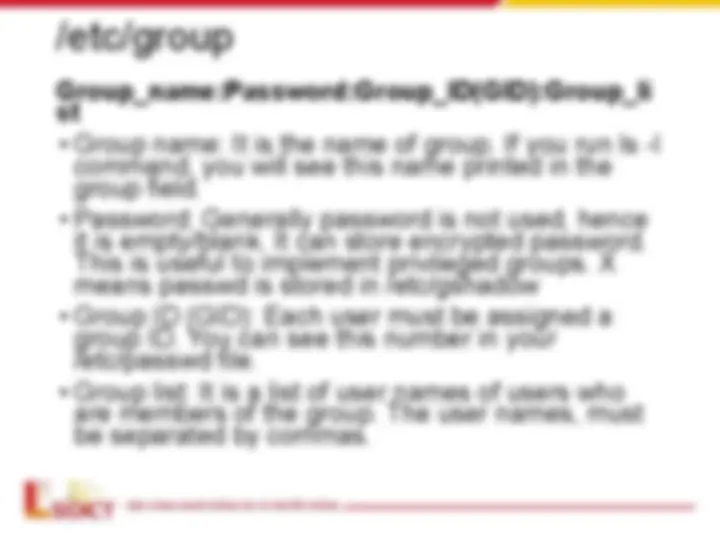
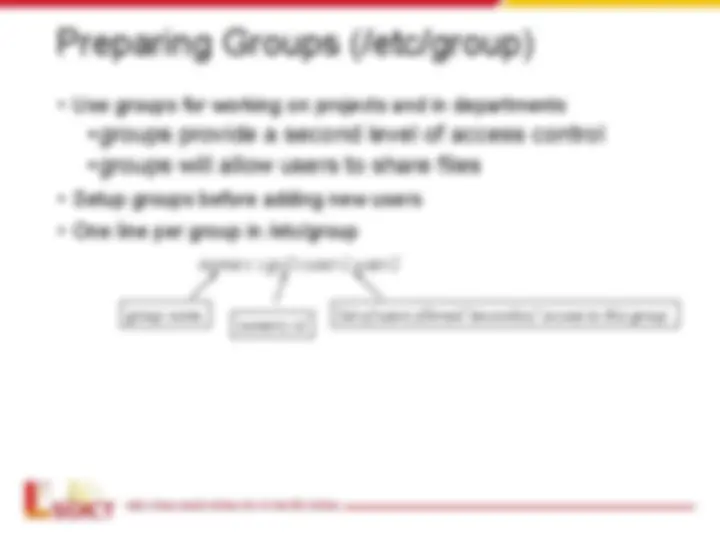
/etc/gshadow
Group_name:Encrypted_password:Group_admin:
Group_members
- Group name — The name of the group. Used by various utility
programs as a human-readable identifier for the group.
- Encrypted password — The encrypted password for the group. If
set, nonmembers of the group can join the group by typing the
password for that group using the newgrp command. If the value of
this field is !, then no user is allowed to access the group using the
newgrp command. A value of !! is treated the same as a value of!
— however, it also indicates that a password has never been set
before. If the value is null, only group members can log into the
group.
- Group administrators — Group members listed here (in a comma
delimited list) can add or remove group members using the
gpasswd command.
- Group members — Group members listed here (in a comma
delimited list) are regular, non-administrative members of the group
11
Root
- Superuser is a privileged account with
unrestricted access to all files and command
- The username of superuser is “root”
- Root has a user ID of 0
- There are two ways to become the superuser
- Login as root directly
- Execute command su to change privileged
● % su
13
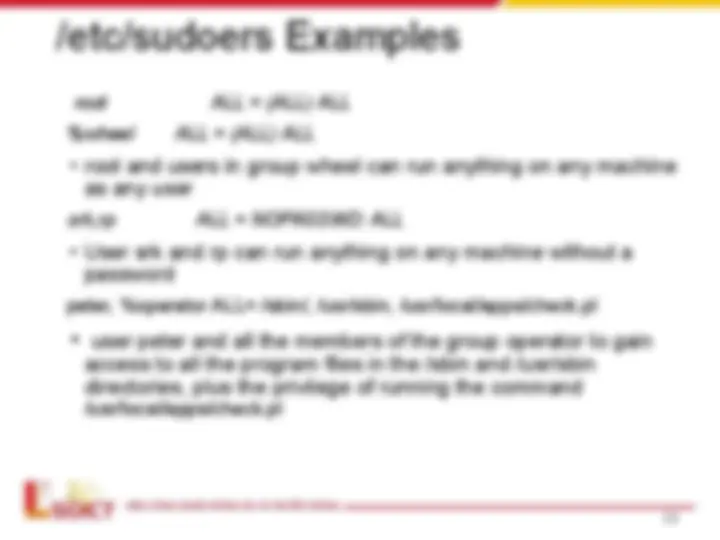
/etc/sudoers Examples
root ALL = (ALL) ALL
%wheel ALL = (ALL) ALL
- root and users in group wheel can run anything on any machine as any user
srk,rp ALL = NOPASSWD: ALL
- User srk and rp can run anything on any machine without a password
peter, %operator ALL= /sbin/, /usr/sbin, /usr/local/apps/check.pl
- user peter and all the members of the group operator to gain access to all the program files in the /sbin and /usr/sbin directories, plus the privilege of running the command /usr/local/apps/check.pl
14
Using Aliases in the sudoers File
User_Alias ADMINS = millert, mikef, dowdy
ADMINS ALL = NOPASSWD: ALL
- User alias ADMINS are user millert.mikef,dowdy
- User alias ADMINS can run anything on any machine without a password
Cmnd_Alias PRINTING = /usr/sbin/lpc, /usr/bin/lprm
Cmnd_Alias SHUTDOWN = /usr/sbin/shutdown
srk ALL = PRINTING, /usr/bin/adduser
- User srk can use printer and add new user
Managing Users
- utility to manage users
- adding users: #useradd or #adduser
- modifying user details: #usermod
- Managing passwords: #passwd
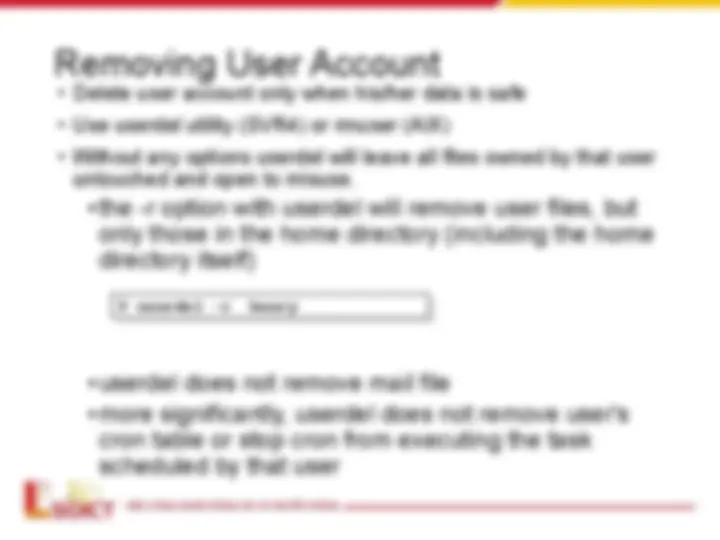
- deleting users: #userdel
Adding Users
- Should not edit the /etc/passd manually
- Utility useradd creates required record in /etc/passwd and /etc/shadow files
- Useful options to useradd to override defaults -u uid specify new user id (default: next available number) -g group specify default group (default other, GID=1) -c comment description of user (default blank) -d dir home directory -m make home directory (recommended otherwise /home/username is not created) -s shell specify login program
- Each user's personal directory is placed in the /home directory. The
directory name will be the same as their user name
- Useadd needs to add an initial password using command passwd seperatedly.
- Other ultility adduser can ask for parameters and passwords iteractively
useradd -m henry
useradd -u 321 -g 152 -m -s /bin/bash bill
Setting Passwords
- New user accounts have to have an initial password
- If new user is added by useradd command, passwd command is needed
- Use the standard passwd program with a username
- as root you will not be prompted for an existing password
- choose a simple password and inform the user verbally
- Fore user to change password at first login
- Lock the user account
passwd -l henry
passwd henry
new password: retype password:
passwd –e henry
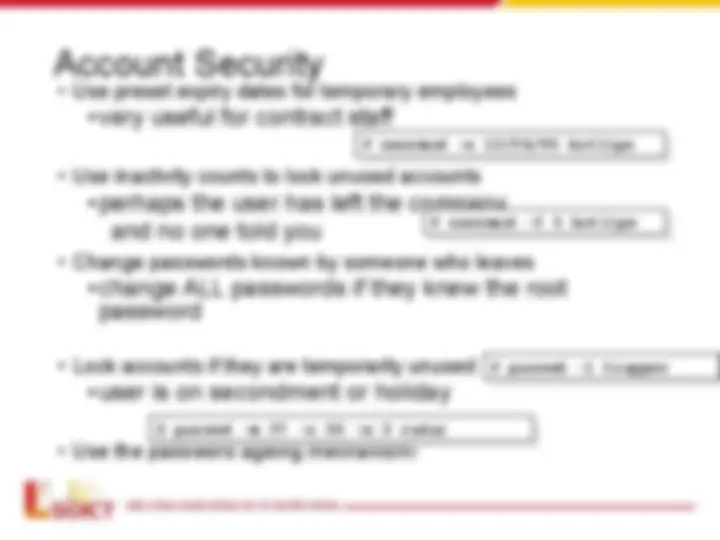
Account Security
- Use preset expiry dates for temporary employees
•very useful for contract staff
- Use inactivity counts to lock unused accounts
•perhaps the user has left the company
and no one told you
- Change passwords known by someone who leaves
•change ALL passwords if they knew the root
password
- Lock accounts if they are temporarily unused
•user is on secondment or holiday
- Use the password ageing mechanism!
passwd -l trapper
passwd -m 27 -x 30 -w 3 radar
usermod -e 12/24/05 hotlips
usermod -f 5 hotlips