












Study with the several resources on Docsity

Earn points by helping other students or get them with a premium plan


Prepare for your exams
Study with the several resources on Docsity

Earn points to download
Earn points by helping other students or get them with a premium plan
Community
Ask the community for help and clear up your study doubts
Discover the best universities in your country according to Docsity users
Free resources
Download our free guides on studying techniques, anxiety management strategies, and thesis advice from Docsity tutors
This document about Coordination and Agreement, Mutual exclusion, Elections and agreement, R-Multicast using coordination and agreement, Introduction, Rationale for this lecture.
Typology: Lecture notes
1 / 24

This page cannot be seen from the preview
Don't miss anything!

















-^
-^
-^
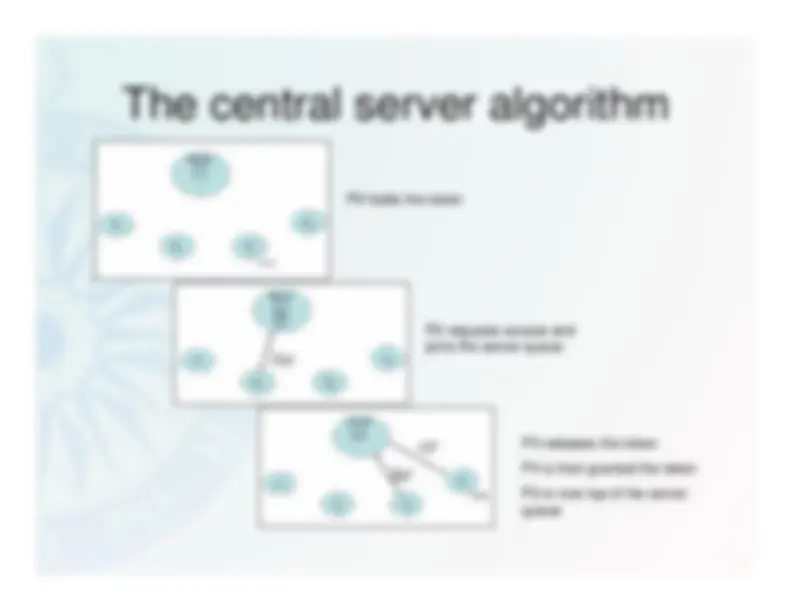
P3 holds the token
P2 requests access andjoins the server queue
P3 releases the tokenP4 is then granted the tokenP2 is now top of the serverqueue
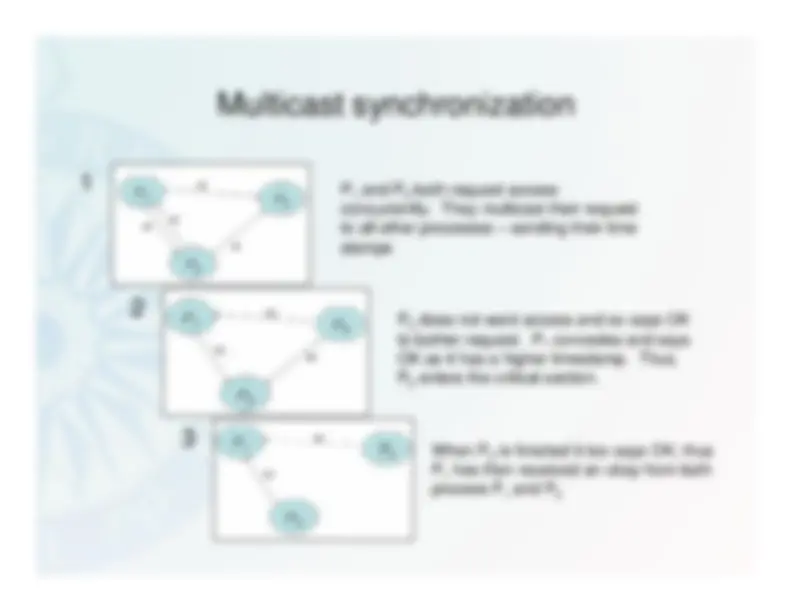
Multicast synchronization
Three processes P
, P 1
and P 2
3
P^1
and P
both want access to a critical section at the same time 2
They timestamp their requests using their clocks and multicast to otherprocesses.Only when they get a response from all other process to they enter thecritical section
Multicast synchronization
P^1
and P
both request access 2
concurrently. They multicast their requestto all other processes – sending their timestamps
P^3
does not want access and so says OK to bother request. P
concedes and says 1
OK as it has a higher timestamp. Thus,P^2
enters the critical section. When P
is finished it too says OK, thus 2
P^1
has then received an okay from both process P
and P 1
3
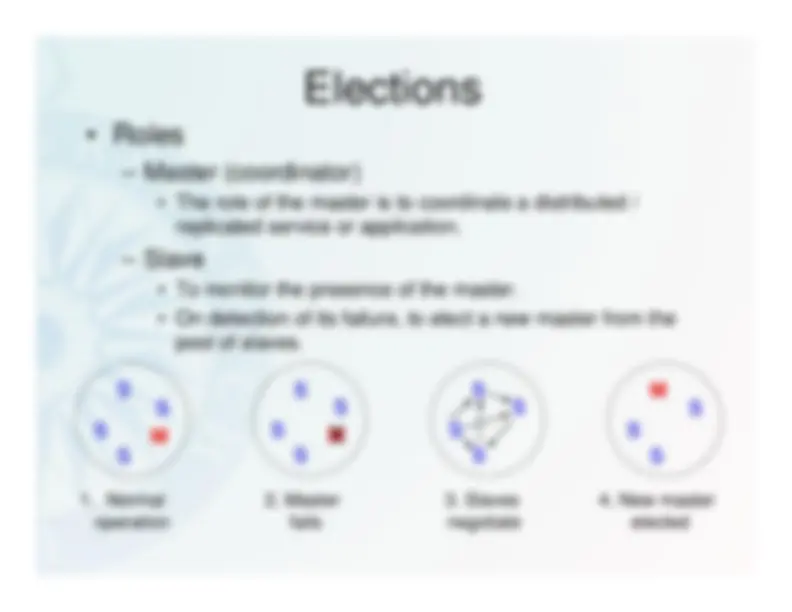
S
M
S
S
S
S
M
S
S
S S
S
S^
M S
S
S
Normal
operation
fails
negotiate
elected
-^
replicated service or application.
pool of slaves.
The proportion of time that a master exists should bevery high.
-^
A replacement must be found quickly if the currentmaster is removed.
-^
Multi-master scenarios must be detected and resolvedquickly.
-^
Spurious elections caused by falsely detecting masterfailure should be avoided.
-^
Normal-mode communication complexity must be low.
-^
Election-mode communication complexity must be low.
-^
Communications overhead (the mean totalcommunication bandwidth required by the electionalgorithm) must be low.
Functional requirements
This algorithm using 3 message types:^ – coordinator:
-^
announcement to all processes with lower IDs
sent to processes with higher IDs
answer to “election”
-^
If answer is not received within a time bound then the sender of“election” sends “coordinator” message
-^
Otherwise, the process waits for T’ to receive a “coordinator”message
-^
If no message arrives, it begins a new election.
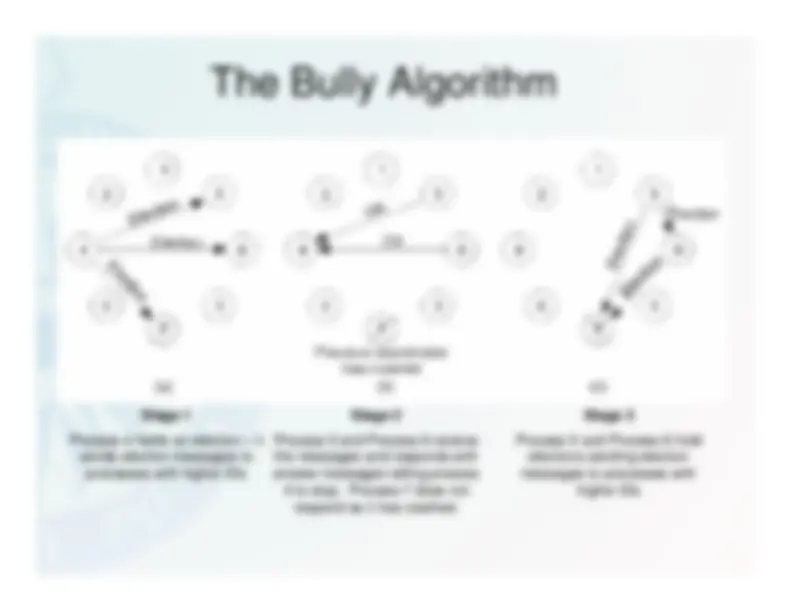
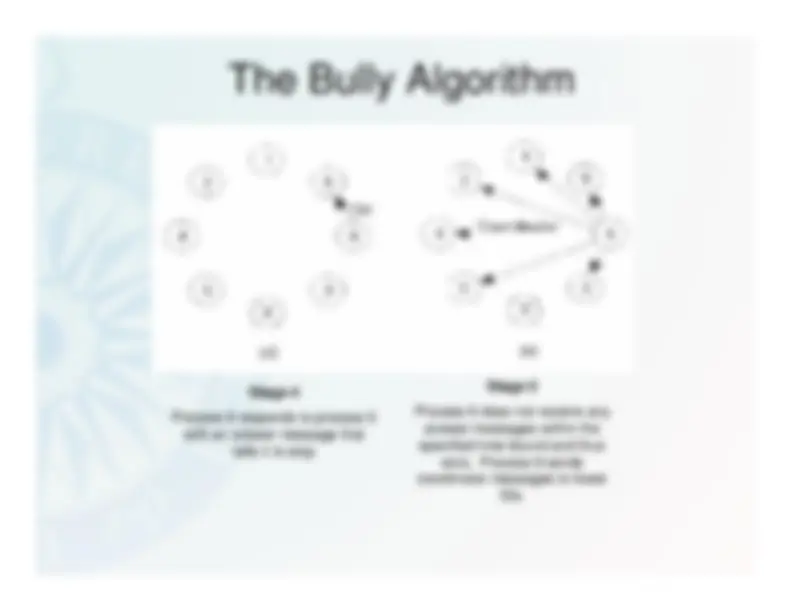
The Bully Algorithm
Stage 1
Process 4 holds an election – itsends election messages to
processes with higher IDs
Stage 2
Process 5 and Process 6 receivethe messages and responds withanswer messages telling process4 to stop. Process 7 does not
respond as it has crashed.
Stage 3
Process 5 and Process 6 holdelections sending electionmessages to processes with
higher IDs
Similar to the bully algorithm, but the nodes arearranged in logical ring.
-^
Nodes only communicate with their logical neighbours.
-^
When the master is lost, its neighbours will notice (lackof periodic messages).
-^
The nodes pass messages around the ring (in severalrounds) to establish which is the highest numberednode and to ensure consensus.
The Ring Algorithm
S(4) 1. Normaloperation
M(7)
S(2)
S(1)
S(5)
fails S(4)
M(7)
S(2)
S(1)
S(4) S(2)
S(1)
S(5)
S(4) S(2)
S(1)
S(5)
chosen andconsensus isreached.
S(4) 5. Node 5takes overas master. S(2)
S(1)
M(5)
The Bully Algorithm
Multicast and Agreement
coordination and agreement
B-multicast
the use of a 1-1 send operation (B-Muliticast)
process in groups
message