

















Study with the several resources on Docsity

Earn points by helping other students or get them with a premium plan


Prepare for your exams
Study with the several resources on Docsity

Earn points to download
Earn points by helping other students or get them with a premium plan
Community
Ask the community for help and clear up your study doubts
Discover the best universities in your country according to Docsity users
Free resources
Download our free guides on studying techniques, anxiety management strategies, and thesis advice from Docsity tutors
This a Assignment 1 of Data structure and Algorithm. #btec #greenwich #datastructure&algorithm #IT
Typology: Assignments
1 / 30

This page cannot be seen from the preview
Don't miss anything!























GREENWICH | GCS
ASSIGNMENT 1
ASSIGNMENT 1 FRONT SHEET Qualification BTEC Level 5 HND Diploma in Computing Unit number and title Unit 19: Data Structures and Algorithms Submission date Date Received 1st submission Re-submission Date Date Received 2nd submission Student Name Tran Nguyen Tan Sang Student ID GCS Class GCS0804_NX Assessor name Le Ngoc Thanh Student declaration I certify that the assignment submission is entirely my own work and I fully understand the consequences of plagiarism. I understand that making a false declaration is a form of malpractice. Student’s signature Tan Sang Grading grid P1 P2 P3 M1 M2 M3 D1 D
Qualification BTEC Level 5 HND Diploma in Business Unit number Unit 19 : Data Structures and Algorithms Assignment title Examine and specify ADT and DSA Academic Year 2021 Unit Tutor Issue date Submission date IV name and date Submission Format: Format: The submission is in the form of an individual written report and a presentation. This should be written in a concise, formal business style using single spacing and font size 12. You are required to make use of headings, paragraphs and subsections as appropriate, and all work must be supported with research and referenced using the Harvard referencing system. Please also provide a bibliography using the Harvard referencing system. Submission Students are compulsory to submit the assignment in due date and in a way requested by the Tutors. The form of submission will be a soft copy in PDF posted on corresponding course of http://cms.greenwich.edu.vn/ Note: The Assignment must be your own work, and not copied by or from another student or from books etc. If you use ideas, quotes or data (such as diagrams) from books, journals or other sources, you must reference your sources, using the Harvard style. Make sure that you know how to reference properly, and that understand the guidelines on plagiarism. If you do not, you definitely get fail Assignment Brief and Guidance: Scenario : You work as in-house software developer for Softnet Development Ltd, a software body-shop providing network provisioning solutions. Your company is part of a collaborative service provisioning development project and your company has won the contract to design and develop a middleware solution that will interface at the front-end to multiple computer provisioning interfaces including SOAP, HTTP, JML and CLI, and the back-end telecom provisioning network via CLI. Your account manager has assigned you a special role that is to inform your team about designing and implementing abstract data types. You have been asked to create a presentation for all collaborating partners on how ADTs can be utilised to improve software design, development and testing. Further, you have been asked to write an introductory report for distribution to all partners on how to specify abstract data types and algorithms in a formal notation.
Tasks Part 1 You will need to prepare a presentation on how to create a design specification for data structures, explaining the valid operations that can be carried out on the structures using the example of:
P1. Create a design specification for data structures explaining the valid operations that can be carried out on the structures. ❖ Abstract data type: − Abstract Data type (ADT) is a type (or class) for objects whose behavior is defined by a set of value and a set of operations. − The definition of ADT only mentions what operations are to be performed but not how these operations will be implemented. It does not specify how data will be organized in memory and what algorithms will be used for implementing the operations. It is called “abstract” because it gives an implementation-independent view. The process of providing only the essentials and hiding the details is known as abstraction. − The user of data type does not need to know how that data type is implemented, for example, we have been using Primitive values like int, float, char data types only with the knowledge that these data type can operate and be performed on without any idea of how they are implemented. So, a user only needs to know what a data type can do, but not how it will be implemented. Think of ADT as a black box which hides the inner structure and design of the data type. Now we’ll define three ADTs namely List ADT, Stack ADT, Queue ADT. ✓ Student ADT: − Properties of Student:
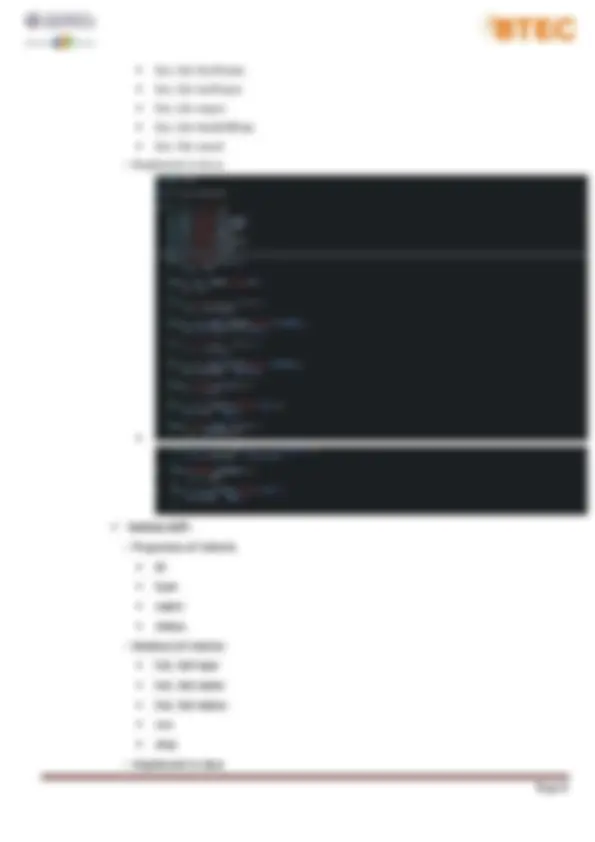
✓ Dog ADT: − Properties of Dog:
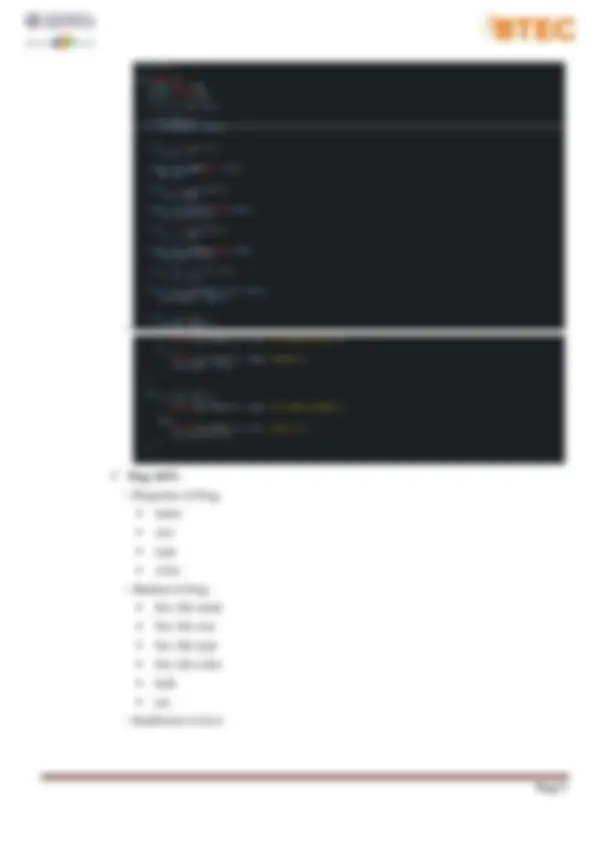
P2. Determine the operations of a memory stack and how it is used to implement function calls in a computer. I. What is memory stack: − A stack can be implemented in a random access memory (RAM) attached to a CPU. The implementation of a stack in the CPU is done by assigning a portion of memory to a stack operation and using a processor register as a stack pointer. The starting memory location of the stack is specified by the processor register as stack pointer. II. Operations: − A Stack contains elements of the same type arranged in sequential order. All operations take place at a single end that is top of the stack and following operations can be performed:
− Output: − M1. Illustrate, with an example, a concrete data structure for a First in First out (FIFO) queue. I. Definition of Queue: − Like Stack, Queue is a linear structure which follows a particular order in which the operations are performed. The order is First In First Out (FIFO). A good example of queue is any queue of consumers for a resource where the consumer that came first is served first. − The difference between stacks and queues is in removing. In a stack we remove the item the most recently added; in a queue, we remove the item the least recently added. II. Queue Representation − As we now understand that in queue, we access both ends for different reasons. The following diagram given below tries to explain queue representation as data structure − − As in stacks, a queue can also be implemented using Arrays, Linked-lists, Pointers and Structures. For the sake of simplicity, we shall implement queues using one-dimensional array. III. Basic Operations: − Queue operations may involve initializing or defining the queue, utilizing it, and then completely erasing it from the memory. Here we shall try to understand the basic operations associated with queues
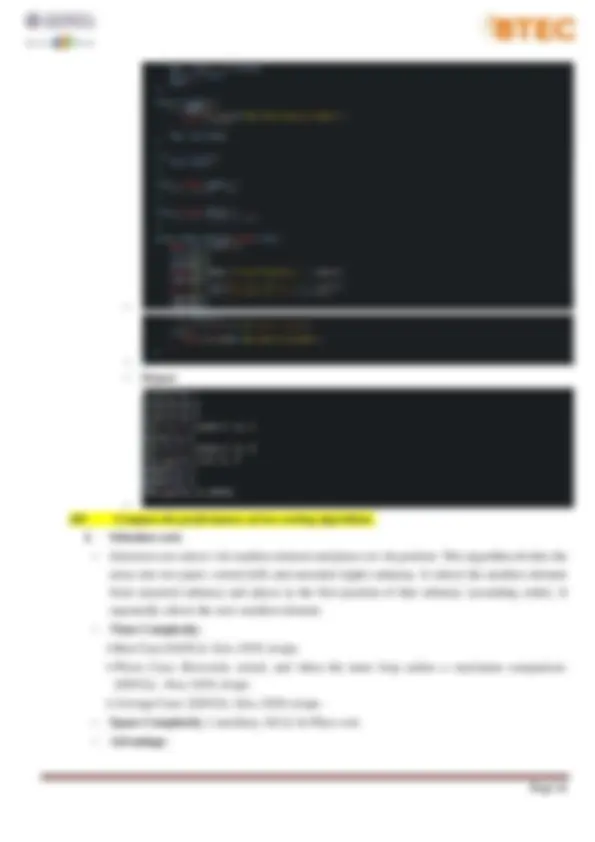
1.It can also be used on list structures that make add and remove efficient, such as a linked list. Just remove the smallest element of unsorted part and end at the end of sorted part. 2.The number of swaps reduced. O(N) swaps in all cases. 3.In-Place sort. − Disadvantage :
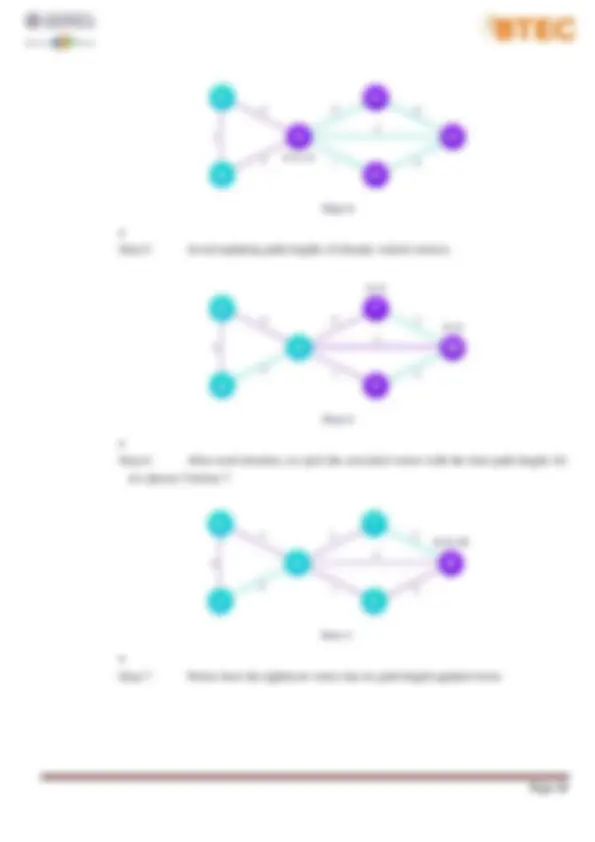
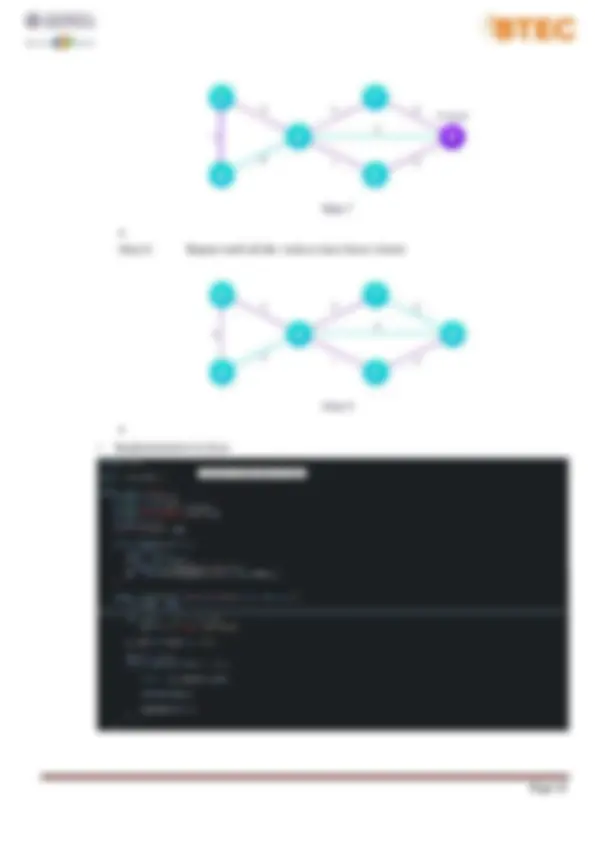
4.Stable sort: does not change the relative order of elements with equal keys. 5.In-Place sort. − Disadvantage : 1.Bubble sort is comparatively slower algorithm. − Implementation in Java: Output: D1. Analyze the operation, using illustrations, of two network shortest path algorithms, providing an example of each. I. Dijkstra's algorithm: − Dijkstra's algorithm has many variants but the most common one is to find the shortest paths from the source vertex to all other vertices in the graph. − Algorithm Steps: Step 1. Set all vertices distances = infinity except for the source vertex, set the source distance = 0. Step 2. Push the source vertex in a min-priority queue in the form (distance, vertex), as the comparison in the min-priority queue will be according to vertices distances. Step 3. Pop the vertex with the minimum distance from the priority queue (at first the popped vertex = source). Step 4. Update the distances of the connected vertices to the popped vertex in case of "current vertex distance + edge weight < next vertex distance", then push the vertex Step 5. with the new distance to the priority queue. Step 6. If the popped vertex is visited before, just continue without using it. Step 7. Apply the same algorithm again until the priority queue is empty. − Example: Step 1. Start with a weighted graph
Step 5. Avoid updating path lengths of already visited vertices ▪ Step 6. After each iteration, we pick the unvisited vertex with the least path length. So we choose 5 before 7 ▪ Step 7. Notice how the rightmost vertex has its path length updated twice
Step 8. Repeat until all the vertices have been visited ▪ − Implementation in Java: