




Study with the several resources on Docsity

Earn points by helping other students or get them with a premium plan


Prepare for your exams
Study with the several resources on Docsity

Earn points to download
Earn points by helping other students or get them with a premium plan
Community
Ask the community for help and clear up your study doubts
Discover the best universities in your country according to Docsity users
Free resources
Download our free guides on studying techniques, anxiety management strategies, and thesis advice from Docsity tutors
Rivest, Adi Shamir, and Leonard M. Adleman, all at the Massachusetts Institute of. Technology, construct the first public-key cryptosystem, the RSA algorithm.
Typology: Summaries
1 / 7

This page cannot be seen from the preview
Don't miss anything!




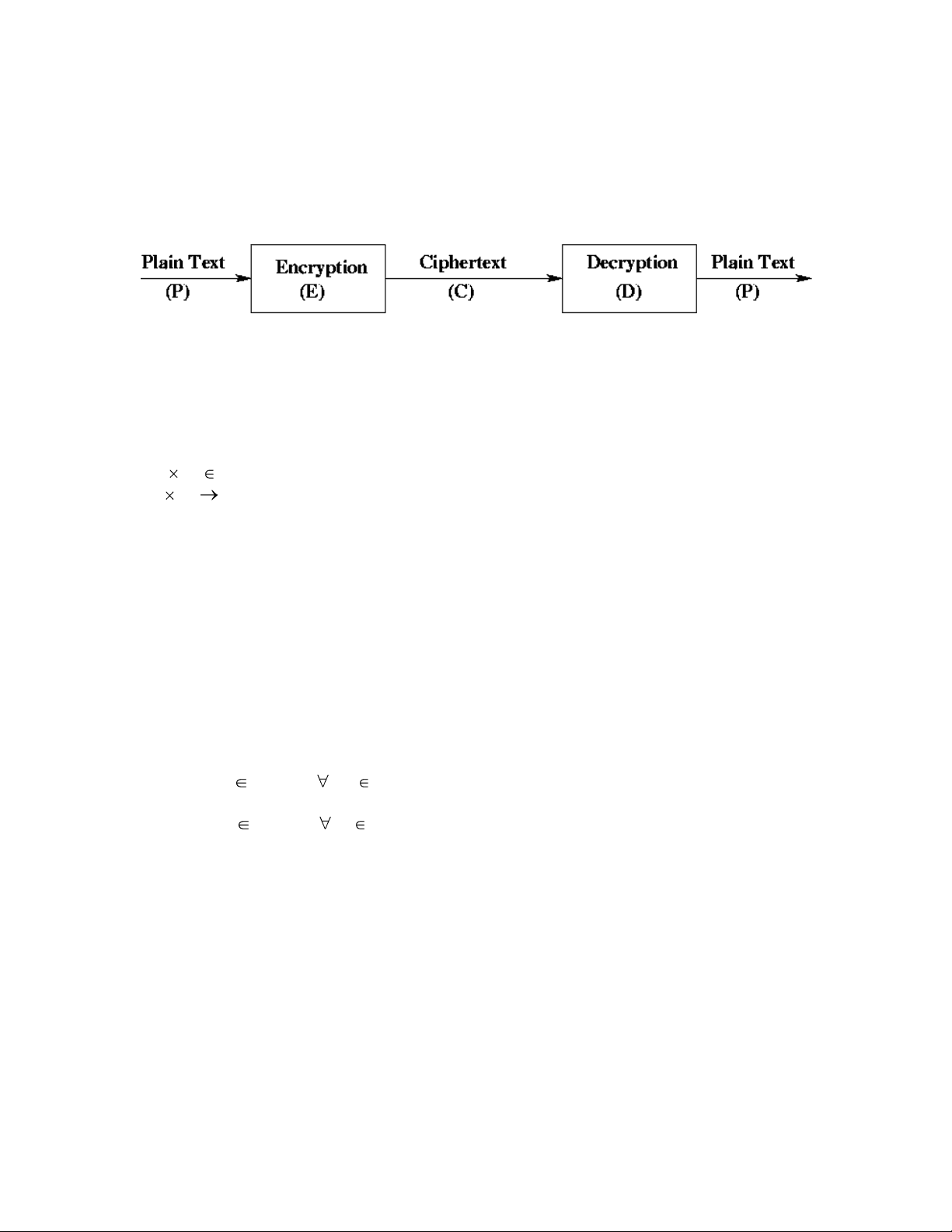
Cryptography comes from the two Greek words meaning “secret writing” and and is the art and science of concealing meaning. Cryptanalysis is the breaking of codes. Basically, what we have is
A classical example of a cryptosystem is the Caesar cipher where letters in the plaintext are shifted to get the ciphertext. Suppose that we have the message “GO CLEMSON”, and we want to encrypt that message using the Caesar cipher. Our key might be 2. The plaintext “GO CLEMSON” would turn into the ciphertext “IQ ENGOUQP”. Our cryptosystem would be:
The goal of cryptography is to keep enciphered information secret. We assume that an adversary wishes to break a ciphertext. Standard cryptographic practice is to assume that the adversary knows the algorithm
Al-Kindi, an Arab scholar and mathematician living in Baghdad, writes Manuscript for Deciphering Cryptographic Messages. It has the first known description of frequency analysis and other cryptanalysis techniques.
1586 Thomas Phelippes uses frequency analysis to decrypt messages between Mary I of Scotland and conspirators against Elizabeth I of England. Mary and the conspirators are all executed.
Major Joseph O. Mauborgne of the U.S. Army and Gilbert Vernam of AT&T Bell Laboratories invent the one-time pad, in which the random, secret key is as long as the message itself and is only ever used once.
1944 At Bietchley Park in England, Colossus (the first vacuum-tube-based, programmable computing machine) decrypts German High Command messages, providing invaluable information prior to the D-day invasion of Normandy.
1945 Claude Shannon of AT&T Bell Laboratories proves that the one-time pad is unbreakable even against an adversary with unlimited computational power. This definition of secrecy is so strong, however, that he also proves that the one-time pad is the only possible cryptosystem satisfying it.
1976 Whitfield Diffie and Martin E. Hellman, both at Stanford University, propose public-key encryption and authentication.
1977 Ronald L. Rivest, Adi Shamir, and Leonard M. Adleman, all at the Massachusetts Institute of Technology, construct the first public-key cryptosystem, the RSA algorithm.
August 1977 In Martin Gardner’s Scientific American column, Rivest et al. challenge readers to decrypt a message encrypted by the RSA algorithm with a 129-digit key (RSA-129). They estimate that doing so may take 40 quadrillion years.
1982 Shafi Goldwasser and Silvio Micali, then PhD students at the University of California, Berkeley, developed the definitional foundations of modern cryptography, including a practical definition of security.
1985 Goldwasser, Micali, and Charles Rackoff of the University of Toronto invent zero-knowledge proofs. A year late Oded Goldrecih of Technion Israel Institute of Technology in Haifa, Avi Wigderson of the Hebrew University of Jerusalem, and Micali devise the zero-knowledge proof for graph three- colorability
1987 Goldreich, Wigderson, and Micali construct protocols for multiparty computation, or secure function evaluation, building on a two-party protocol developed by Andrew C. Yao of Princeton University.
1994 Netscape Communications releases the Secure Sockets Layer protocol, which employs public-key encryption to provide security for transaction on the World Wide Web.
1994 Arjen K. Lenstra of Bell Communications Research and more than 600 volunteers on the internet, using about 1,600 computers running recently developed factoring algorithms, take eight months to factor RSA-129. They reveal the message, “THE MAGIC WORDS ARE SQUEAMISH OSSIFRAGE.”
2008 An RSA key of recommended length (2,048) would take more than a quadrillion years to break on a modern PC.
In 1976 a new approach to cryptosystem was proposed where there was one key to encrypt the plaintext and a different key used to decrypt the ciphertext. The key used to encode the message is public, i.e. it is know to the world. The key that is used to decode the encoded message is private, i.e. this key is only known to the individual. Pictorially we have
3 Characteristics
The above depiction of encoding and decoding a message using public and private keys can be expressed as
P = D ( KPub, E(KPri, P))
where KPri is the private key and KPub is the public key.
Note: The Public & Private key can be applied in either order.
There are two classical symmetric key ciphers: transposition ciphers and substitution ciphers. We will look at both of these examples.
Transposition Cipher Rearrange the characters in the plaintext to form the ciphertext. The letters are not changed. This is really a permutation function. The best attack is a statistical frequency attack. An example of a transposition cipher is the rail fence cipher.
Rail Fence Cipher
P: H E L L O W O R L D
H L W L E O O D L R
C: H L W L E O O D L R
Susceptible to a frequency of occurrence to discover the transposition
Substitution Cipher A substitution cipher changes the characters in the plaintext to produce the ciphertext. The Caesar cipher is an example of a substitution cipher and is shown below.
Caesar Cipher The idea again with the Caesar cipher is to shift letters n characters with wrap around.
ABCDEFGHIJKLMNOPQRSTUVWXYZ
Let’s do a 4 shift
P H E L L O
C L I P P S
P = C = { all sequences of letters }
K = { I | I is an integer o I 25 }
E = { Ek | k K and p P, Ek(p) = (p + k) mod 26 }
D = { Dk | k K and c C, Dk(p) = (26 + c - k) mod 26 }
Caesar ciphers are susceptible to statistical attacks.
In 1949 Shannon proposed the following characteristics for a good cipher:
This is just common sense in that why spend tons of money on protecting something that has little value?
This implies that we should restrict neither the choice of keys nor the types of plaintext on which the algorithms can work. If the process is too complex, it will not be used. Furthermore, the key must be transmitted, stored, and remembered, so it must be short.
Key Distribution Must be out-of-band Public key can be used to distribute other keys
Speed Fast Slow; typically, 10, times slower than symmetric key
Sender encrypts with her private key. Receiver decrypts with the sender’s public key.
Alice encrypts with her private key. Only she knows her private key.
Bob decrypts with Alice’s public key and knows that the message is authenticate because only Alice knows her private key.
Therefore, the message has been authenticated as being sent by Alice.
Sender encrypts sender’s private key and recipient’s public key
Alice encrypts with her private key and again with Bob’s public key
C = (KBPub, ( KAPri, P))
Bob decrypts with his private key and Alice’s public key.
P = (KAPub, (KBPri, C))
Note:
In practice n is very large ~ 1024, 2048, or 4096 bytes
Note: Symmetric encryption is the work horse x Very fast Addition, Xor, substitution, shifting
Public Key Encryption is used for special applications 10,000x slow multiplication, division